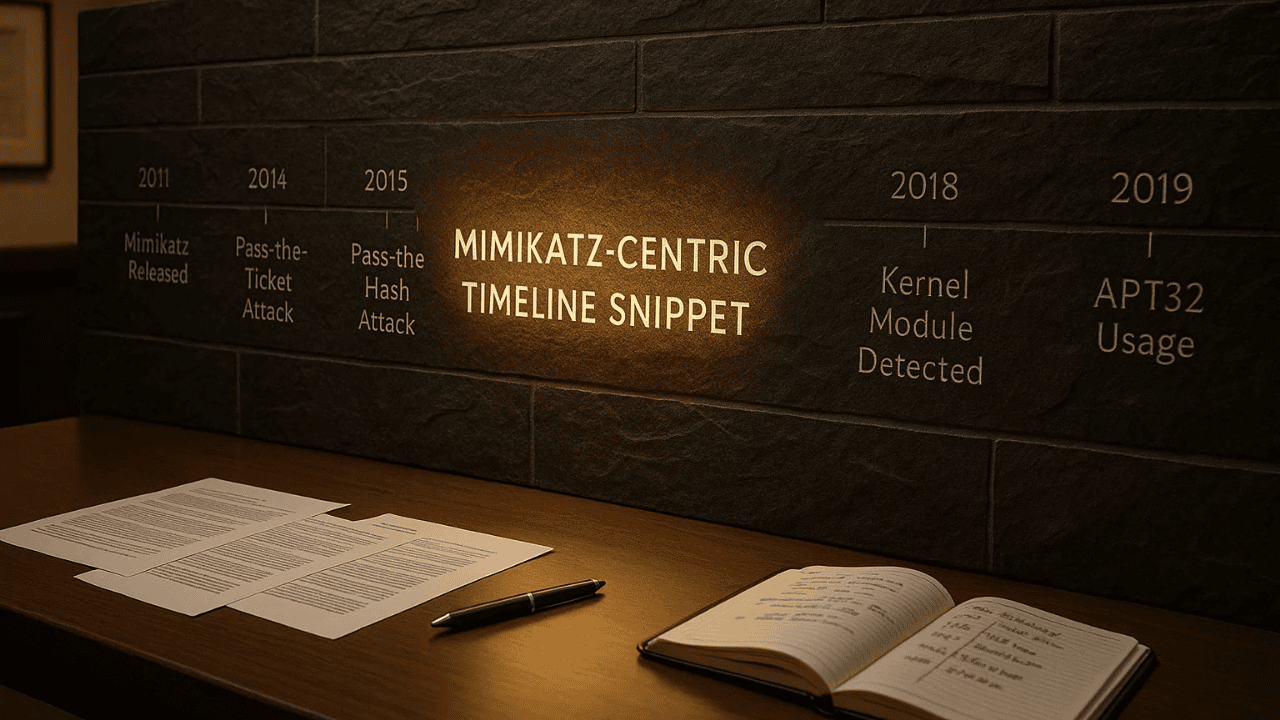
Mimikatz has long been recognized as one of the most influential tools in the world of cybersecurity, shaping how attackers and defenders think about Windows credential security. When exploring the history of this tool, a mimikatz-centric timeline snippet becomes an effective way to understand how a small research project evolved into a globally recognized threat and essential penetration testing utility. This article presents a detailed look at the origins, development, use cases, and defensive lessons derived from more than a decade of its presence. By examining the mimikatz-centric timeline snippet from multiple angles, readers gain clarity on why the tool still matters today and how it continues to influence modern security strategies.
Mimikatz’s journey spans from early curiosity-driven development to widespread adoption in both legitimate and malicious contexts. The mimikatz-centric timeline snippet also reveals how the tool adapted to changes in Windows operating systems and how attackers learned to take advantage of its capabilities. With this foundation, we can better understand why organizations around the world still take the threats posed by credential-dumping techniques seriously.
Origins of Mimikatz and Early Development
The earliest part of any mimikatz-centric timeline snippet has to begin with its creation by Benjamin Delpy, also known by his online name GentilK1wi. Around 2007, Delpy started Mimikatz as a side project focused on exploring Windows authentication internals. His initial experiments were not intended to launch a widespread tool but rather to deepen his own understanding.
By 2011, Mimikatz reached its first notable milestone with the release of version 1.0. This event marks an important entry in the mimikatz-centric timeline snippet because it opened the door for researchers and attackers alike to explore the capabilities embedded within Windows’ credential management.
Soon after its release, Mimikatz began to appear in cyber incidents. One of the earliest publicly referenced examples was its role in aspects of the DigiNotar breach of 2011. Although not the only tool used, Mimikatz contributed to the attackers’ ability to navigate compromised systems, cementing its name in cybersecurity history.
Key points from this early period include:
• The tool originated from personal research rather than malicious intent
• The first release expanded its audience dramatically
• Attackers immediately recognized its value
These factors laid the foundation for the mimikatz-centric timeline snippet as we know it today.
Expansion Through Open-Sourcing and Global Awareness
Another major milestone in any mimikatz-centric timeline snippet came in 2012 when Delpy presented Mimikatz at a security conference. This event was quickly followed by the tool’s release on GitHub, which drastically increased accessibility. As a result, Mimikatz became a dual-use tool: a powerful asset for penetration testers and a dangerous weapon for attackers.
After the open-source release, adoption surged. The mimikatz-centric timeline snippet during this period highlights rapid community growth, continuous feature expansion, and a wave of new use cases. Mimikatz became known for retrieving plaintext passwords, hashes, Kerberos tickets, and other sensitive credential material directly from memory.
Mimikatz gained its reputation not only because of its effectiveness but also because of its simplicity. Attackers and ethical testers with administrative access could leverage powerful features without complex setup. This user friendliness would later contribute to its integration into malware toolkits, automated attack scripts, and red team frameworks.
The Windows Security Response and Continued Evolution
As the mimikatz-centric timeline snippet moves into the Windows 8.1 era, Microsoft began to respond. One of the key defensive actions taken was to allow administrators to disable the WDigest authentication protocol, which previously stored plaintext passwords in memory. This protocol had been one of the primary extraction targets for Mimikatz.
Yet despite these improvements, Mimikatz evolved rapidly. The mimikatz-centric timeline snippet demonstrates that each time Windows removed one avenue of attack, Mimikatz introduced new modules and techniques. For example, the tool expanded functionalities related to Kerberos, enabling Golden Ticket, Silver Ticket, and Pass-the-Ticket attacks.
This back-and-forth pattern between operating system improvements and tool adaptation became a defining feature of the mimikatz-centric timeline snippet, reflecting the constant push and pull between attackers and defenders.
Important techniques Mimikatz introduced include:
• Pass-the-Hash attacks
• Pass-the-Ticket attacks
• Extraction of Kerberos tickets
• Golden Ticket and Silver Ticket creation
• Memory scraping for credential objects
• Windows Security Account Manager exploitation
The continued relevance of these techniques explains why Mimikatz remains widely used today.
Mimikatz in Real-World Cyber Attacks
As cyber threats grew in complexity, the mimikatz-centric timeline snippet increasingly intersected with real-world incidents. From APT-style intrusions to global ransomware attacks, Mimikatz became a staple of adversarial operations.
By the mid-2010s, it appeared in numerous publicly reported breaches. Attackers used it for lateral movement, privilege escalation, and long-term persistence through forged Kerberos tickets. Because Mimikatz could pull credential information from memory directly, it often bypassed traditional security controls.
The mimikatz-centric timeline snippet also shows that many high-profile attacks integrated Mimikatz scripts into automated workflows. Some ransomware families embedded Mimikatz-like code directly into their payloads, enabling credential extraction during the destructive stages of an attack.
For penetration testers and defenders, these events reinforced the importance of monitoring memory access patterns, detecting suspicious authentication anomalies, and implementing least-privilege strategies.
How Mimikatz Became a Dual-Use Tool for Good and Bad
The most interesting part of the mimikatz-centric timeline snippet revolves around its dual nature. While attackers found it incredibly valuable, Mimikatz also became a standard tool for ethical hacking and red team engagements.
Security professionals rely on Mimikatz to:
• Evaluate the strength of Windows and Active Directory setups
• Identify misconfigurations and vulnerable authentication pathways
• Demonstrate real-world attack chains to clients
• Validate security improvements after remediation
This dual purpose is what makes the mimikatz-centric timeline snippet so unique. Few tools have such wide adoption across both malicious and legitimate sectors.
Modern Significance and Why Mimikatz Still Matters
Even today, the mimikatz-centric timeline snippet indicates that Mimikatz remains highly relevant. Though Windows has implemented more protective measures, many environments still contain misconfigurations or legacy systems that are vulnerable to credential extraction attacks.
Additionally, defenders now use Mimikatz-like behavior as detection triggers. Behavioral analytics and advanced monitoring systems often look for suspicious memory reads or unusual authentication actions that mimic Mimikatz activity.
Organizations continue to harden their systems through:
• Disabling legacy authentication protocols
• Enforcing robust credential protection features
• Implementing managed service account strategies
• Updating domain controllers and Kerberos policies
• Limiting administrative access and session sharing
These strategies are all informed by lessons learned throughout the mimikatz-centric timeline snippet.
Future Outlook on Credential Security and Tool Evolution
As cybersecurity evolves, so will tools like Mimikatz. The mimikatz-centric timeline snippet hints at a future where credential theft methods may shift toward more covert or cloud-based approaches. However, Mimikatz’s legacy will continue to influence how both offensive and defensive teams prepare for modern threats.
The growing integration of identity protection systems, hardware-based credential guards, and zero-trust principles may reduce Mimikatz’s effectiveness in some environments. Yet misconfigurations, outdated systems, and poor security hygiene will continue to make it a relevant threat.
Conclusion
A mimikatz-centric timeline snippet offers an insightful perspective into the evolution of one of the most influential tools in cybersecurity history. From its humble beginnings as a personal research project to its widespread adoption by both attackers and defenders, Mimikatz has shaped how organizations think about credential security. Its adaptability, powerful features, and ongoing presence in cyber incidents demonstrate why understanding its journey is important for anyone responsible for protecting Windows environments. By studying the mimikatz-centric timeline snippet, security professionals can better prepare for modern threats and build stronger defenses against credential theft and post-exploitation attacks.
FAQs
- What is the purpose of a mimikatz-centric timeline snippet?
It provides a chronological overview of the development, use, and influence of Mimikatz, helping readers understand its evolution and significance. - Why is Mimikatz still used today?
It remains effective in environments where misconfigurations or legacy systems expose sensitive credential data, making it valuable for both attackers and penetration testers. - How does Mimikatz retrieve credentials?
It accesses memory areas where Windows stores authentication details, allowing extraction of plaintext passwords, hashes, and Kerberos tickets. - Are there defenses against Mimikatz attacks?
Yes. Implementing credential guard, disabling legacy authentication, patching systems, and limiting administrative privileges can significantly reduce risk. - Is Mimikatz considered malicious?
It is a dual-use tool. While attackers misuse it, security professionals use it for legitimate testing and evaluation of system security.